With the growth of remote workforces, secure remote access has become a priority for IT. SSL VPNs offer granular access control while keeping users connected to network applications.
As a bonus, clientless access uses web clients to connect, which means it can be accessed on any device without proprietary software. It also simplifies maintenance and updates.
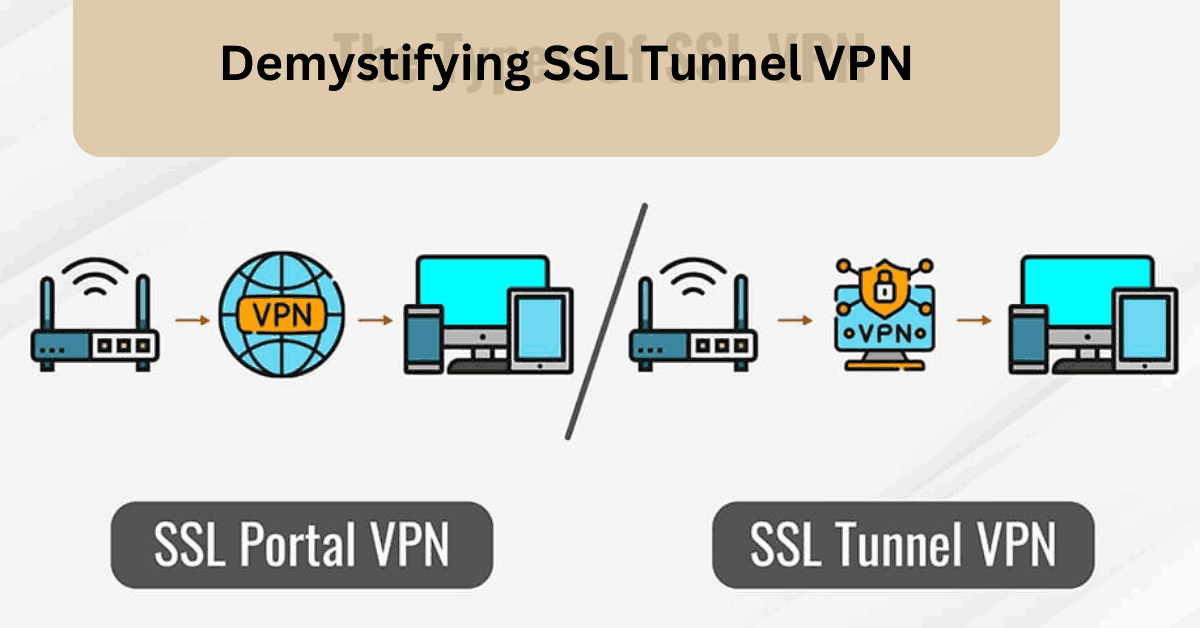
What is an an SSL VPN?
In simple terms, an SSL VPN connects users over the Internet to a company network, encrypting traffic along the way. This virtual private network can access web-based SaaS applications, local utilities and storage hosted on organizational hardware, or client-server apps.
It can be configured to tunnel only specific applications or networks, reducing costs and complexity. It also allows a more flexible connection since SSL is natively supported by most devices, unlike traditional IPSec VPNs that require dedicated hardware and software.
SSL VPNs use the TLS (transport layer security) protocol implemented in modern web browsers, eliminating the need for a dedicated client app to install and maintain. The SSL connection also creates a secure circuit that can’t be compromised by man-in-the-middle attacks and is updated when the browser or operating system is updated.
As the work-from-home movement grows, SSL VPNs are becoming more important. However, it’s important to understand the strengths and limitations of this technology. SSL VPNs can be cheaper and easier to manage than IPSec VPNs, but they don’t offer the same level of security or connectivity.
They are also limited to a single web browser session, meaning the encrypted connection ends when you close the browser. In addition, many malware attacks target browsers, making SSL VPN connections vulnerable to phishing scams and other malware attacks.
Why SSL VPN?
SSL (Secure Socket Layer) is a widely used encryption protocol that can be combined with VPN connectivity to provide enhanced security for remote access users and ease of use.
Unlike IPsec VPN, which operates at the network layer, SSL connects to web services and applications at the transport layer and encrypts data for transmission over the Internet.
It can be accessed using standard web browsers, eliminating the need for standalone software clients and hardware integration.
Because an SSL tunnel VPN uses standard web browsers, it is also easier to manage and maintain. As a result, organizations can scale their remote access VPN to fit their organizational needs without the cost of dedicated infrastructure. SSL also offers compatibility with various operating systems and devices, including mobile phones.
While the simplicity of an SSL tunnel VPN can be beneficial, it has some drawbacks regarding security. Because it only works through a web browser, malware attacks such as man-in-the-middle attacks and adware are more likely to target users. They typically target the browser, which can open various files on the user’s device.
Moreover, an SSL tunnel VPN can only connect to web-enabled applications, which limits the user’s ability to access physical network resources such as printers. However, this can benefit in some instances as it allows for more precise management of user privileges.
Implementation
SSL Tunnel VPN requires a web browser to establish a connection, which makes it more convenient for remote users and devices that can’t install client software, like mobile devices, tablets and some point-of-sale equipment.
When the device connects to an organization’s portal, it opens a secure ‘tunnel’ that allows users to access their materials without needing general internet traffic to pass over the VPN, which can cause a significant drop in performance.
This model is also good for security because it limits lateral movement across the organization by tunneling only to specific applications rather than the entire network. It can make it easier to manage privileges and prevent security breaches.
However, it’s important to remember that this solution isn’t foolproof. It is still possible for data traces to be left on the device after an SSL Tunnel VPN session has closed, such as temporary files, cookies and spooler directories.
As such, it’s vital to implement two-factor authentication (2FA), endpoint security tools and policies to reduce the risk of breaches. Also, suppose users, in that case, access a virtual desktop through an SSL Tunnel VPN.
In that case, they can run risky applications on their computer, such as keyloggers, that could potentially expose credentials or confidential information to attackers. For this reason, the virtual desktop provision in an SSL Tunnel VPN should be subject to posture checking and only allow users whose devices meet certain prerequisites to gain access.
Security
As the number of remote workers grows and enterprises adopt work-from-home cultures, secure remote access solutions are critical to ensure that workers can stay connected to their organization’s applications and data.
Leading secure remote access solutions adapt to any tech setup, confirm user identities with MFA, and evaluate each login with device trust, regardless of whether the worker is onsite, remote or on the go.
An SSL VPN establishes a secure connection between the remote device and the VPN server by encrypting all traffic between them using SSL protocol.
This encryption process takes place at the application layer of the OSI model, which is separate from the IP packet-level protocols used on the Internet. All network metadata between the device and the VPN server is securely encrypted; no attacker can intercept or decipher it.
In addition, many SSL VPN products also include features that expand the security offered by a standard web browser alone.
These portal and tunnel features enable the VPN to connect to non-websites and other network services that aren’t typically accessible through a web browser.
It allows users to access local files stored on servers at the enterprise remotely, SaaS applications hosted on the cloud, and more — all via a secure SSL tunnel. SSL VPNs also reduce the risk of a breach by limiting the attack surface of the corporate network.
Unlike IPSec VPNs, which provide full network access for remote workers, SSL VPNs create tunnels to specific applications and limit what the worker can see or do within that tunnel to the minimum necessary.